The Dynamics 365 security model is designed to ensure data integrity and privacy with restricted access control mechanisms and an efficient role-based security design. It focuses on providing controlled access to data where only the users who have the appropriate authorization can access and perform data operations. It lets you closely mirror your real-world organizational structure by creating business units, teams, and individual user accounts, each assigned with a particular user role.
It also makes sure data sharing and collaboration are enabled, albeit under secure authorizations and user privileges. Users are prevented from accessing data that they do not own and can only deal with data on a need basis. Therefore, data compliance and confidentiality regulations can be easily upheld.
While the Dynamics 365 security configuration is shipped with certain default options, you can customize the security configuration as per your particular needs. Let us give you an overview of all the essential default options and how best to customize them to fit your needs.

Security Default Dynamics 365
Before getting into tweaking your existing security configuration, you should have a clear understanding of the various security roles and privileges.
A security role is used to identify a user’s role within the organization. It can be related to their job or position in the company hierarchy, such as manager, sales representation, IT admin, and so on.
.png)
Whenever you create a new user account, you will have to assign a security role to the user account to decide the various privileges they can have with respect to your data entities. For instance, a user assigned with the manager’s role will have access to data records within his subordinate reporting structure but will not be able to access data from another department. Similarly, a service technician will have minimal access to customer records and may only have read-only access to customer data.
The data access rights assigned to each security role forms its set of privileges. A security role can be assigned two types of privileges names:
Record Level Privileges
These define the particular rights such as read, write, edit, create, assign, share, and more that can be performed on a particular data record.
Task-Based Privileges
These privileges are required to perform data-based tasks such as publishing a post, making forms go live, and so on.
The user security role can also define the access level assigned to the user, which can be:
- Global – Access to all records within an organization
- Deep – Access to a business unit and its subordinate business units’ data records
- Local – Access to data records within the user’s business unit
- Basic – Access to records owned by the user
- None – No access allowed.
When users form a part of a team, they will also automatically be assigned the team privileges to access the team’s data.
Dynamics 365 Security Configuration: How To Create A New Custom Security Role?
The predefined security roles are designed keeping in mind the best security practices and a lot of research. So, as a basic rule, it is recommended that you do not manipulate existing security roles but create your custom security roles for customized requirements. There is yet another set of security roles installed by the D365 application services, which cannot be updated.
To create new security roles, you must have the necessary access level and privileges assigned to you. In general, the system administrator security role is the apt user role that can be used to perform these operations. This security role has all the necessary privileges to create and assign security roles.
Here are the steps to creating a custom security role:
For demonstration sake, we will only assign privileges to access a custom data entity called ‘security role’ to this custom role.
- Log in as a System administrator and make sure you have the necessary privileges
- To check your existing security role, visit your user profile.
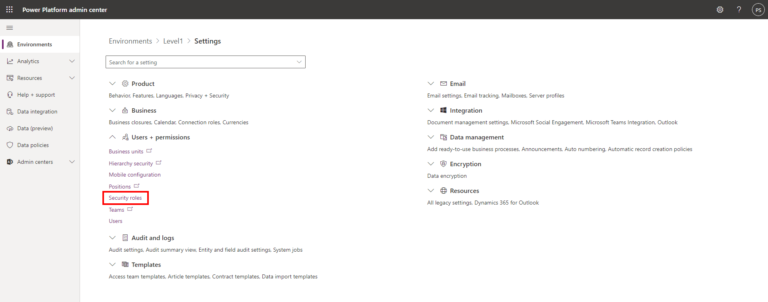
- Select an environment under the Power Platform Admin Center
- Choose Settings > Users + Permissions > Security Roles and create a New security role
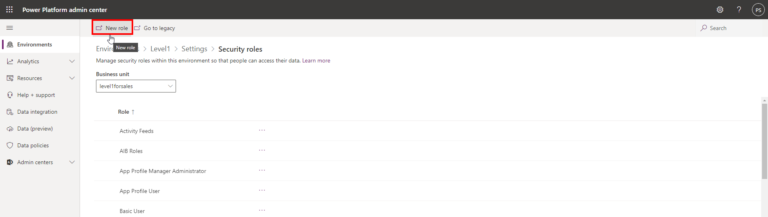
- Name your role and then click the Business Management Tab
- You can see the various entities and set the corresponding entity privileges from the entity list.
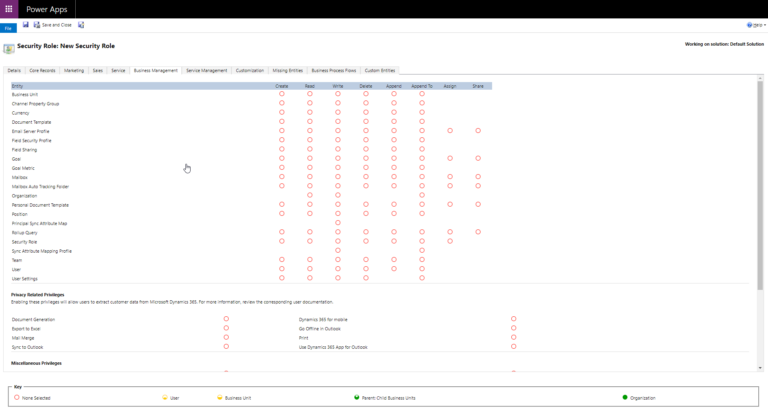
- Choose the Security Role Entity and set the privileges such as Create, Read, Write, Delete, and more with the appropriate access level such as Business Unit, Organization, and more.
- Save your changes
Now you have created a new security role that can be assigned to any user account. Once assigned, the user will have the set privileges as configured under the entity privileges.
Dynamics 365 Security Configuration: How To Assign The New Security Role?
Follow these steps to assign a new security role to the user account. Let us choose an admin-level user for the task.
- Choose an environment under the Power Platform Admin Center
- Choose Settings > Users + Permissions > Users and select the user account. You can select ad admin user account
- Choose Manage Roles under the user and select the new security role.
- You can now select all the security roles you want to assign to other users and click OK.
How To Give Authorization To The Dynamics 365 Security Configuration
To give access to a particular user to make the security configuration settings, that user needs to have the privileges of a System Administrator. So a system admin should first assign the system admin role to a user to make the required security configuration setting changes.
Here are the steps to authorize a user to be able to make security configuration changes:
- Log in as a system administrator
- Select an environment under the Power Platform Admin Center
- Click Settings > Users + Permissions > Users.
- Select a user and go to Manage Roles
- Assign the System administrator role to the user and click OK
Conclusion
Even the mightiest of tools require the right wielder to reach its maximum potential. The Dynamic 365 CRM platform is one powerful platform, but its efficiency and performance depend on how well you can use it.
Let us guide you into making the right choices and defining the security roles and privileges tailored to your particular needs. Our experts will help you leave all worries with configuration and simply get on to using this fantastic platform without wasting your precious productive hours. Contact us now for any queries on Dynamic 365 security configuration
Liked what you just read? Sharing is caring.

November 13, 2025 by Kooldeep Sahye by Kooldeep Sahye Marketing Specialist
Fuelled by a passion for everything that has to do with search engine optimization, keywords and optimization of content. And an avid copywriter who thrives on storytelling and impactful content.


